ESSENTIAL EIGHT: Application PATCHING
Posted By Dipankar Chakravarty, On 16 Sept 2023.
- Cyber Security
- Essential 8
- Data Protection
- Application Whitelisting
- Shadow IT
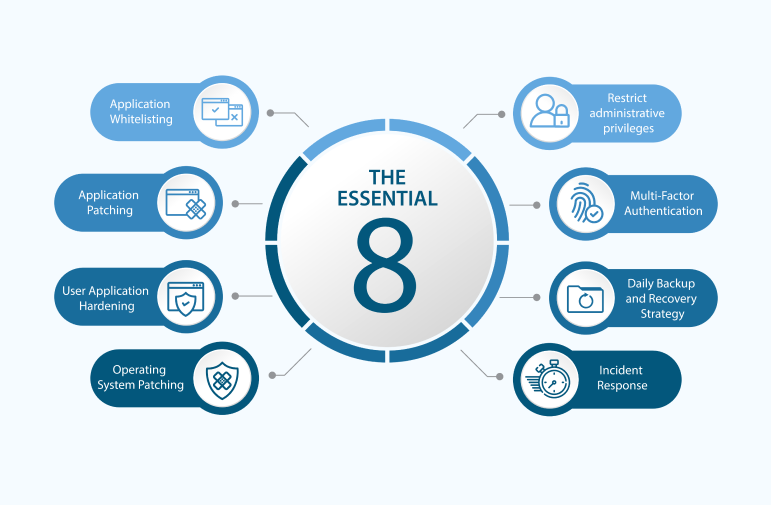
The Essential Eight is a cybersecurity framework developed by the Australian Cyber Security Centre (ACSC) to provide organizations with a set of strategies to mitigate cybersecurity risks. Application patching plays a crucial role in several of the Essential Eight strategies, specifically in the "Patching Applications" and "Configuring Microsoft Office Macro Settings" strategies.
Here's how application patching fits into the Essential Eight:
The reason application patching is one of the key elements of Essential Eight strategy on its own as business use a plethora of IT tools and application store, disseminate and utilise data to run and operate the business. Patching Applications, which can be defined as a strategy which emphasizes the importance of promptly applying security patches to operating systems, applications, and devices to protect against known vulnerabilities. This strategy helps in plugging vulnerability gaps within a business which are using various IT tools across the business.
Application patching should be a fundamental component of any cyber security strategy. It involves regularly updating and patching software applications, including operating systems, web browsers, office suites, and other software. By doing so, organizations can address known security vulnerabilities and reduce the risk of exploitation by cyber threats.
Application patching helps maintain a secure and resilient IT environment, reducing the attack surface and minimizing the risk of security breaches. However, this can become a complex process depending on the IT environment and needs specialised policy and procedures to manage the same.
Traditionally, businesses have deployed application patching using a combination of manual and automated processes. Here's a breakdown of the traditional methods and practices for application patching:
1. Risk Assessment and Planning
IT administrators or teams would manually identify which patches were available for their operating systems, applications and third party applications like (web browser, java, .net run time and adobe flash player). This often involved monitoring vendor websites, security bulletins, and mailing lists for patch notifications.
2. Manual Deployment
As the complexity of IT environments grew, many businesses started using automated patch management tools to streamline the process. These tools offer the following advantages:
-
Patch Deployment Scheduling
Automation tools allow businesses to schedule patch deployment during non-business hours, reducing disruptions.
-
Patch Testing
These tools often include testing features, enabling businesses to test patches in a controlled environment before rolling them out to production systems.
-
Reporting and Compliance
They provide reporting capabilities, helping organizations track and document their patching activities for compliance purposes.
-
Patch Rollback
Some tools offer the ability to roll back patches if issues arise after deployment.
4. Product development
Get insights into what are the customer requirements and how the current products or services can be improved. This information can shape the organisation’s future product development efforts.
5. Enhance customer Experience
By understanding the customers better, the organisation may look forward to personalize their experiences and create long-lasting relationships.
While traditional patch management methods have been effective, they can be time-consuming and resource-intensive, especially for larger organizations. As a result, many businesses have increasingly turned to automated patch management solutions and cloud-based services to streamline the process and enhance their cybersecurity posture.
Remember that application patching is an ongoing process, and it's crucial for the security and stability of your business's IT infrastructure. Even without a dedicated IT department, by following simple steps and being proactive, you can minimize the risks associated with unpatched software.
Android and iOS updates are indeed excellent examples of application patching in the mobile operating system environment. Where all users on a regular basis update their phones to protect from new vulnerabilities and get enhanced features.
By combining open-source patch management tools with manual methods, you can create a robust and proactive approach to patching applications, ensuring that you stay up-to-date with security patches and protect your systems from vulnerabilities.
Open-Source Patch Management Tools:
- OpenVAS (Open Vulnerability Assessment System)
- OSSIM (Open Source Security Information and Event Management)
- OVAL (Open Vulnerability and Assessment Language)
Open-Source Patch Management Tools:
-
- Join mailing lists and subscribe to security advisories for the open-source software you use. This ensures you receive timely notifications of security vulnerabilities.
-
- Regularly visit the official websites or repositories of the open-source software to check for updates and security patches.
-
- Changelogs provide information about what has been fixed in each release. Review these to identify security-related changes.
-
- Before applying patches, verify their authenticity by downloading them from official sources or trusted repositories.
-
- Always back up the configuration and data associated with the software before applying patches to ensure you can recover the system if issues arise.
-
- Download the patches from official sources and apply them manually. This may involve using tools like patch or diff to apply changes to the source code.
-
- If the software is compiled from source code, recompile and rebuild it after applying patches.
-
- After patching, thoroughly test the software to ensure that the patch did not introduce new issues or break existing functionality.
-
- Maintain detailed records of the patching process, including which patches were applied, when, and any issues encountered. This documentation is crucial for auditing and troubleshooting.
-
- Update your inventory and documentation to reflect the changes made due to the patching process.
-
- Make patch management a routine task by scheduling regular checks for updates and security patches for your open-source software.
-
- Educate your team on the importance of regularly patching open-source software and the security benefits it provides.
By combining open-source patch management tools with manual methods, you can create a robust and proactive approach to patching applications, ensuring that you stay up-to-date with security patches and protect your systems from vulnerabilities.
Application patching and VAPT (Vulnerability Assessment and Penetration testing) are both essential components of a comprehensive cybersecurity strategy. Application patching focuses on keeping software up-to-date with known fixes, while VAPT proactively identifies vulnerabilities, including both known and unknown ones. Together, they help organizations maintain a strong security posture and minimize the risk of security breaches.
In summary, application patching is a critical component of the Essential Eight cybersecurity framework, particularly in strategies that emphasize the importance of promptly applying security patches to mitigate known vulnerabilities. Regularly patching both operating systems and applications helps organizations reduce their cybersecurity risk and maintain a strong security posture.



